Governance, Risk, and Compliance (GRC) is a key framework for ensuring that organizations operate with integrity, efficiency, and resilience. Within this framework, Vendor Risk Management (VRM) plays a critical role by addressing the risks posed by third-party vendors and suppliers. As businesses rely increasingly on external partnerships to deliver key services and solutions, the potential vulnerabilities introduced by these relationships require proactive and systematic management.
Integrating VRM into a GRC framework strengthens an organization’s ability to manage external risks while maintaining compliance and operational stability. VRM is not just an isolated process; it enhances the overall effectiveness of GRC by ensuring that third-party relationships align with governance principles, risk management strategies, and regulatory requirements.
What is Vendor Risk Management?
Vendor Risk Management (VRM) refers to the systematic process of overseeing and mitigating the risks associated with third-party vendors. These risks can stem from financial instability, data security vulnerabilities, regulatory non-compliance, or operational inefficiencies within a vendor’s processes. Effective VRM ensures that vendors meet an organization’s standards for security, compliance, and performance.
The core activities in VRM include:
- Risk Identification: Determining potential vulnerabilities in vendor relationships.
- Risk Assessment: Evaluating the impact and likelihood of identified risks.
- Risk Mitigation: Implementing strategies to minimize or eliminate risks.
- Ongoing Monitoring: Continuously tracking vendor security and compliance.
By adopting VRM practices, businesses can foster stronger, more secure relationships with their vendors.
The Role of VRM in Governance, Risk, and Compliance (GRC)
Vendor Risk Management (VRM) is an integral component of Governance, Risk, and Compliance (GRC) frameworks. By aligning vendor overview with governance principles, risk management strategies, and compliance requirements, VRM strengthens the overall integrity of an organization’s operations. Here’s how VRM fits into the three core pillars of GRC:
Governance: Establishing Standards and Policies
Governance in the context of GRC involves defining policies and standards that guide an organization’s operations and relationships. VRM supports governance by:
- Developing Vendor Policies: Establishing clear guidelines for vendor selection, performance benchmarks, and acceptable risk levels.
- Vendor Accountability: Ensuring vendors understand and comply with the organization’s governance requirements.
- Consistency Across the Supply Chain: Implementing governance practices across all vendor relationships to uphold ethical and operational standards.
For example, an organization might mandate that all vendors follow specific cybersecurity protocols or sign contractual agreements that include compliance clauses.
Risk Management: Identifying and Mitigating Threats
Risk management focuses on identifying potential threats and implementing strategies to address them. VRM enhances this process by proactively managing risks specific to vendor relationships, including:
- Risk Identification: Conducting thorough assessments to uncover vulnerabilities such as weak cybersecurity practices or financial instability.
- Risk Mitigation: Developing tailored strategies to address vendor risks, such as requiring encryption for sensitive data or implementing alternative suppliers to minimize dependency.
- Risk Monitoring: Continuously evaluating vendor performance and adapting risk management strategies to address emerging threats.
Integrating VRM within a GRC framework ensures that vendor-related risks are managed alongside internal risks, creating a holistic approach to organizational security.
Compliance: Meeting Regulatory and Legal Standards
Compliance ensures that an organization and its vendors adhere to industry regulations, legal requirements, and ethical standards. VRM supports compliance by:
- Regulatory Adherence: Ensuring vendors meet regulatory requirements such as GDPR, HIPAA, PCI DSS, or other industry-specific standards.
- Documentation and Audits: Maintaining records of vendor assessments and audits to demonstrate compliance during regulatory reviews.
- Proactive Compliance Management: Monitoring changes in regulations and updating vendor agreements and requirements accordingly.
For instance, a healthcare organization relying on vendors for data processing must ensure that these vendors comply with HIPAA standards to avoid regulatory fines and data breaches.
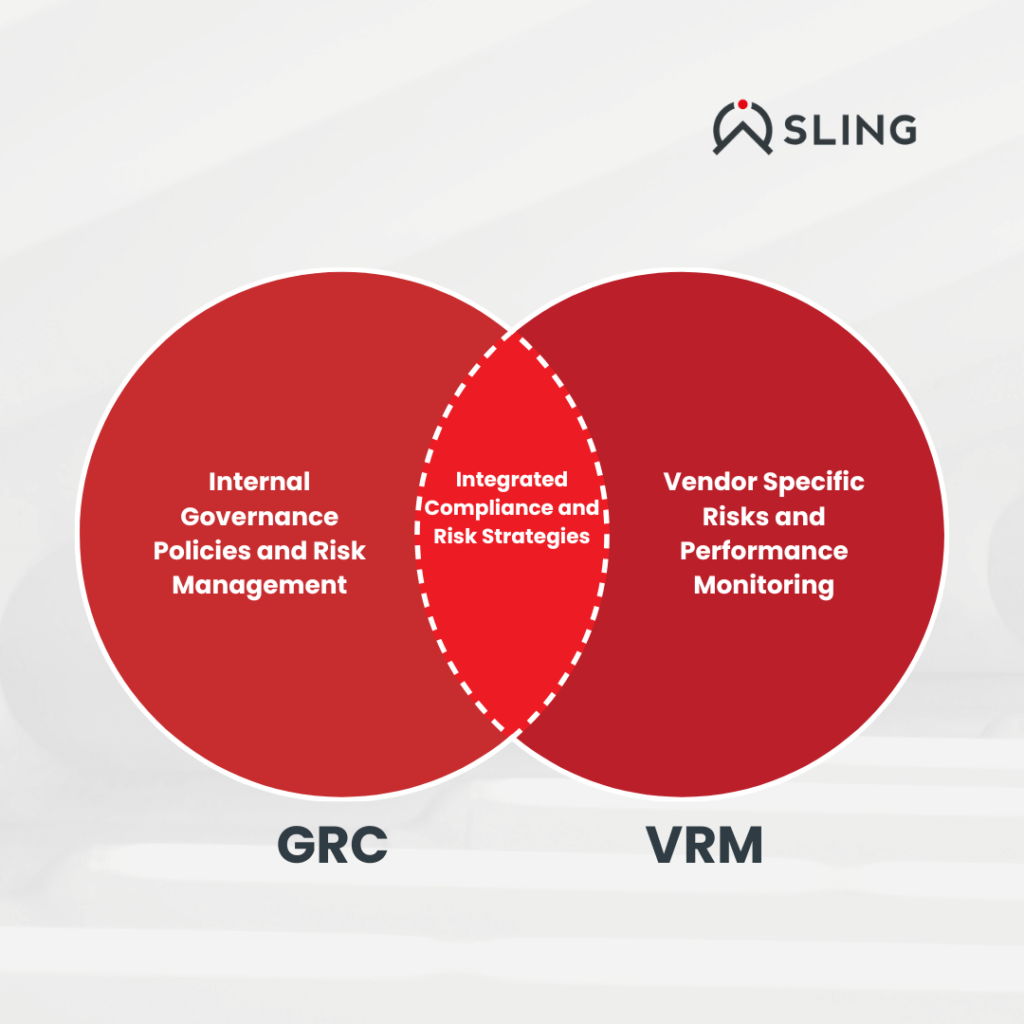
How GRC and VRM Work Together
By integrating VRM into a GRC framework, organizations achieve:
- Centralized Oversight: A unified system to manage governance, risk, and compliance for both internal operations and third-party vendors.
- Enhanced Decision-Making: Better insights into vendor risks allow for informed decisions and proactive measures.
Stronger Security Posture: Comprehensive management of vendor risks reduces the likelihood of breaches, fines, and reputational harm.
Benefits of Incorporating VRM into GRC
| Benefit | Impact |
| Risk Visibility | Better identification and mitigation of vendor-related risks. |
| Compliance Assurance | Improved regulatory adherence and audit readiness. |
| Operational Continuity | Reduced supply chain disruptions and enhanced preparedness. |
| Reputational Protection | Safeguards the organization’s brand and public trust. |
| Cost Efficiency | Avoids fines, reduces incident costs, and optimizes resource usage. |
Organizations that prioritize vendor risk management within their GRC strategies are better equipped to thrive in today’s complex and interconnected business environment. And avoid exposing themselves to regulatory penalties, operational disruptions, and damage to stakeholder trust.



